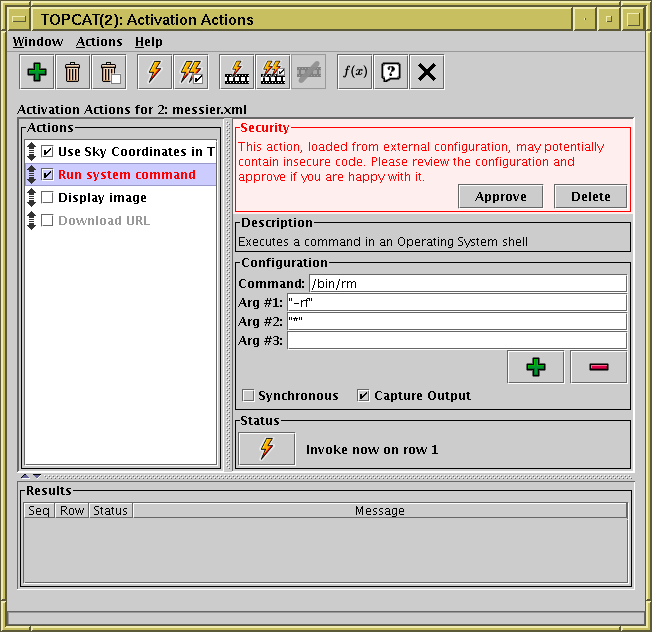
Activation Window configured with security implications
Activation actions can be configured to perform a wide variety of user-defined actions, in some cases including actions that could have damaging consequences. For instance the Run System Command action can execute arbitrary system (shell) commands with the permissions of the user running the TOPCAT application. As long as the TOPCAT user is the person who has configured these commands, this is no more dangerous than the same user sitting down at the keyboard to type shell commands.
In the case of Activation Actions that have been loaded from a Session file however, it is possible that the person who saved the session might have configured it to perform malicious actions affecting whoever re-loads it. TOPCAT can't determine whether an action is actually malicious, but it can identify actions which could be configured to do malicious things. In the case that it detects an Activation Action that has been loaded from a Session file that might be doing something dangerous (invoking arbitrary system commands, or in general anything that has effects outside of the TOPCAT application itself, excepting some known-harmless SAMP messages) it will ask the user for explicit approval before invoking it.

Activation Window configured with security implications
This screenshot shows what happens. When called upon to invoke a potentially dangerous pre-configured action, it displays the Security panel in red, and the user has to click the Approve button before the action will be invoked. If you see this, you should, as instructed, check that the action configuration is not doing anything it shouldn't. Once you have approved it, the security panel will disappear and later invocations will take place with no further user interaction.
If you know that the session file is harmless, and you don't
want to be bothered by these approval messages, you can use the
Approve All Actions (![]() ) menu item
in the Actions menu.
) menu item
in the Actions menu.
The Run System Command
and Execute Code
actions can trigger these warnings for fairly obvious reasons.
They can however also be triggered under some circumstances by
Display Image,
Load Table and
Plot Table.
That's because in some configurations these actions can allow
file/URL location values that perform preprocessing of the input streams
using the "<syscmd" or "syscmd|" syntax
described in Section 4.2, and that means that referencing
image/table locations either entered directly, or acquired from table data,
could result in execution of arbitrary system commands.
This preprocessing is always switched off by default,
and you shouldn't switch it on unless you need it,
so it will not apply unless you have turned it on explicitly or
loaded it from a session file.
In nearly all cases, you don't need to think about these issues, but if you are loading a session file that may have been prepared by somebody else, TOPCAT will warn you in case anything malicious might be capable of affecting you.